TQ42 Studio: Enterprise-Grade Quantum Innovation
TQ42 Studio offers a unified environment for building, tuning and applying quantum-enhanced solutions at scale, combining cutting-edge quantum research with no-code and SDK options, in a robust and secure innovation workspace.
Join Our Closed Beta Program
While some features and integrations are continuously evolving, with regular improvements and new capabilities being rolled out on an ongoing basis, our community of Beta users plays a key role in defining the future of TQ42 Studio.

One Workspace, Two Paths within TQ42 Studio
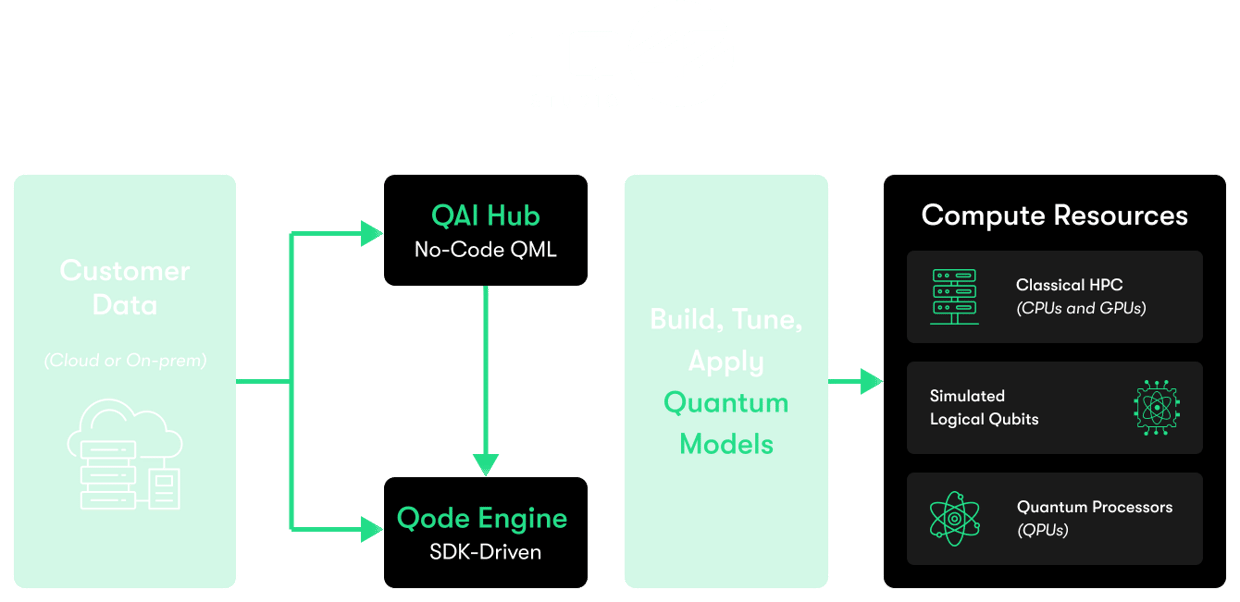
TQ42 Studio Features You'll Be Excited About
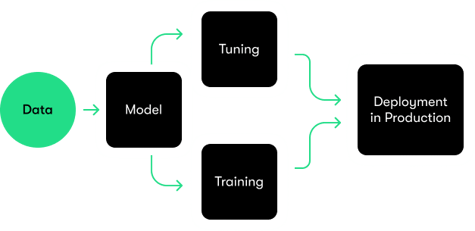
End-to-End Quantum Ecosystem
A fully integrated environment—from data ingestion and experimentation to robust production deployment.
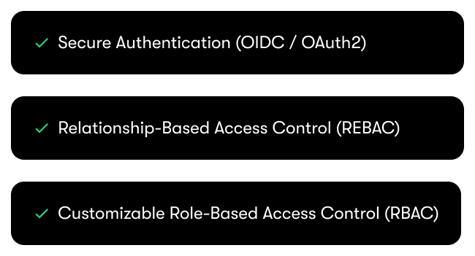
Enterprise-Level Security
Stringent security features including encryption, secure data transfer, and advanced user management.
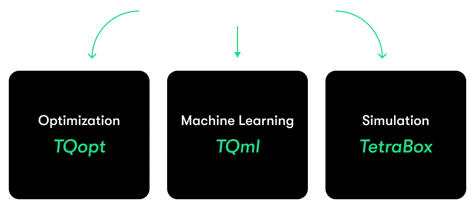
Proven Quantum Expertise
Leverage Terra Quantum’s leading research and cutting-edge quantum libraries.
Flexible and Scalable Deployment
Optimize usage with access to CPUs, GPUs, simulated and native QPUs.

Democratized Innovation
From advanced coders to newcomers, TQ42 Studio caters to all skill levels, accelerating quantum adoption.
-
Industrial Manufacturing Optimization
±5°C improved accuracy in temperature predictions, significantly enhancing operational predictability and efficiency.
-
Renewable Energy Prediction
40% forecasting accuracy boost, optimizing grid performance and energy dispatch.
-
Satellite Mission Optimization
98.5% successful completion rate for high-value tasks, maximizing mission profitability.
-
Material Design Optimization
35% runtime reduction, accelerating chemical R&D cycles.
±5°C improved accuracy in temperature predictions, significantly enhancing operational predictability and efficiency.
40% forecasting accuracy boost, optimizing grid performance and energy dispatch.
98.5% successful completion rate for high-value tasks, maximizing mission profitability.
35% runtime reduction, accelerating chemical R&D cycles.
For individuals and teams exploring quantum AI models.
Includes:
| ✓ | QAI Hub access: No-code Quantum ML model creation with TQ Copilot guidance |
| ✓ | Qode Engine access: Python SDK for building, tuning, and applying quantum models |
| ✓ | 100 free credits, so you can easily experiment with HPC resources—CPUs, GPUs |
| ✓ | Flexible credit packages - top up when you need it and scale your experiments |
| ✓ | Robust documentation and tools so you can collaborate with your team in a secure, easy-to-use environment |
| ✓ | Early Access to TQ Academy preview version |
| ✓ | Upcoming releases: Expect iterative improvements, new beta features, and expanded learning resources |
For scaling teams & production workloads.
Everything in Beta, plus:
| ✓ | QPU access (evolving ecosystem of QPU providers) |
| ✓ | Priority support and dedicated onboarding |
| ✓ | TQ Academy enhanced courses & certification |
| ✓ | Deployment and integration features for production environments |
(Exact Pro features offered with the open launch may vary.)
We also offer tailored Enterprise and Academic plans, each addressing specific needs—from advanced security/compliance to large research collaborations.
Contact us to discuss your specialized requirements. We’ll work with you to define custom usage packages, dedicated support, and any necessary professional services.
Beyond the Platform



Ready to Shape the Future of Quantum ML?
Be a part of our closed Beta. Experiment with no-code quantum ML or try out our Python SDK.
